Digital Intrusion Time Line
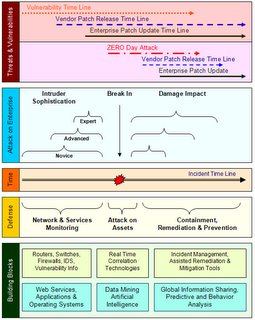
The objective of this article is to identify the issues around a digital intrusion. The following diagram shows the picture of a digital intrusion time line (by an internal or external Intruder or an automated Intruder – virus / worm / bots etc) along with the Vulnerability time line and security monitoring tools with current features and future building blocks. The focus is on the fundamental problems, and it will not go into analyzing different digital attack patterns or any vulnerability analysis.
Latest CERT reports a total of 5990[1] vulnerabilities for the year 2005 an increase of 58.5% from the year 2004 and a 3402% increase from the year 1995. Usually vulnerability in an application is due to un-identified bug in the code. However there are times when backdoors written explicitly in some application to get into a users machine.
An intentional backdoor into any system is more dangerous than an accidental bug due to an oversight or bad coding practices. Huge debate gone over the recent WMF[2] (Windows Meta File) Vulnerability – Microsoft Security Advisory (912840) whether it’s an intentional backdoor or not.
“Speeding up the patch process is never going to solve the problem; it is never going to be fast enough. We need to be investing very heavily in zero-day defenses, because another zero-day will happen. There is a lot of talk about whether (the software vendor has) gotten the patch out in time, but the real conversation should be about risk removal, not risk mitigation.”
Richard Ford, associate professor of computer science, Florida Institute of Technology
“Application vulnerabilities propagate so rapidly today that the old methods of dealing with them no longer suffice. New standards like AVDL offer one of the best hopes of breaking this cycle by dramatically reducing the time between the discovery of a new vulnerability and the effective response at enterprise sites”
John Pescatore - Vice President of Security Research, Gartner
Security Threat Modeling
Security Threat Modeling is an essential process to protect the Assets (or applications). It helps the organizations to determine the correct controls and produce effective counter measures within the budget. Effective management and understanding of the vulnerabilities is required to efficiently defend attacks against those (vulnerabilities). As the number vulnerabilities increases year by year the customer needs a mechanism to identify the most critical vulnerabilities in his enterprise.
The Core of Digital Security
The three key things in digital security for the enterprise are identifying and classifying the Intruder and their attacks on the Assets and the Damage it can cause on the enterprise or the potential damage on the similar attacks in the future. Regulatory compliance and other government regulations revolve around the core or rather monitoring the health of the core.
The above image shows the Intruder attack sophistication and the incident time line which starts when the intruder finds the vulnerability in the enterprise and the actual break-in and the damage he causes by information leakage, denial of service on critical systems, and attack on other systems etc.
The Defense sections shows the 3 phases which is as follows; the Monitoring phase, Attack discovery on the assets and the Containment and the Remediation process. The key will be how efficiently we can correlate and provide relevant information back to the end user at the right time so that he/she (the analyst) can stop the attack (while in progress) before it wrecks havoc in the enterprise.
The three core areas (Intruder, Assets and Damage) will remain same today (2006) or even after 15 or 20 or 2000 years. What matters is how good we are at identifying these three key elements and build a robust Security Threat Model around it.
Intruders and their Attacks
Classification of an Intruder is critical in understanding the Threat the intruder posses. A good Security Threat Model needs to understand the strengths, weakness and the attack methodologies of any Intruder. The Intruders are classified into 3 – Internal, External and Automated (Robotic) Intruder. Classification of Intruders helps us to prioritize the incidents and focus on the relevant incident.
Assets
Security revolves around protecting the Assets (Behind every Asset there will be some applications). Asset oriented Security Monitoring will be the key in this evolution. Application infrastructure of the future will be heavily distributed in nature with SOA (Service Oriented Architecture). Protecting the business services will be the most important aspect in the service oriented world.
Asset Oriented Security Monitoring will eventually move towards applications and in the future will lead to protecting the collection of web services[3] which the applications published. Security will go down to the fabric of the distributed applications. According to Forrester the ERP[4] Market will be $24 Billion by the end of 2008. SAP[5] and Oracle the leading ERP Application providers will be moving to Service Oriented architecture by the end of 2008.
Classification of assets is important to protect the assets efficiently. Asset value will not yield this classification. For example an asset which contains blog and user forum data will be classified differently compared to assets with financial transaction databases. There will be assets which require protection while data at rest[6] as well as protection of data on the wire.
Damage caused by Incidents and its impact
The above chart and depicts the damage impact if a break in happens. Today the users do the impact manually and lot of different software applications will be used in the complete process. Streamlining this business process and using this data to further improve process will help in quick remediation and containment.
Tracking the cost of Incidents, resources required for containment and remediation, and the time spent will help in predicting the actual cost involved if the similar attacks happens in the future. This information can be used in the Security Threat Model to narrow down the attacks and vulnerabilities where the potential damage will be very high.
Digital Security - Building Blocks
The first generation of security management tools processed data from security devices like firewalls, intrusion detection systems, vulnerability scanners apart from network devices like routers and switches. Correlation technologies correlated the events across the systems. However, these systems focused more on handling the events. This model is an extension of log management systems which started of the Digital Security Management space.
The second generation Security Management tools focuses more on entities like Assets and its relevance, Network and its importance, Attacker (with classification) and threat levels, Vulnerability Severity relevant to the network. This model deviates from the first generation event based management as the focus is on the entity rather than the events.
Entity model in the second generation simplifies the process of building a Security Threat Model compared to first generation event model based Risk or Threat Scores. The CSO[7] / CISO are focused more on protecting their assets instead of worrying about how many events passed through the network.
The third generation of Security Management will move closer to where the real action in the enterprise digital world – ‘The Applications’. As per the Forrester and Gartner[8] most of the enterprise applications will move towards SOA[9] (Service Oriented Architecture) by the end of 2008-2009. Cisco already announced the Cisco AON (Application Oriented Network) Architecture where the focus is on routing the application specific traffic.
End of the day security is all about protecting the data (information or knowledge) created by the applications (Assets in the enterprise) and the applications runs 24/7.
The Fourth generation of Security Management will see the convergence of physical security with information security. As per Forrester forecast[10] Security Convergence spending for Europe and North America combined will be $11 Billion dollars in 2008 compare to $506 million in 2004.
Conclusion
The objective of this article is to highlight the core of digital security and the expectations around the core. Around 30-40 years ago we knew that the fundamentals of Atom[11] are electron, proton and neutron. As the science progressed we realized that protons and neutrons were made up of quarks[12] and discovered hundreds of sub atomic particles[13] and then finally to ‘Strings’ and the String theory[14], However, electrons, protons and neutrons still remains as fundamental particles (at atomic level).
So, let me re-instate the core (AID) again.
Intruders (Know your enemy)
Damage
Do we think the above three elements will change in the year 2131[15]. The answer is a big ‘NO’.
There will never be a silver bullet which will solve all the problems. What you can do is to improve the probability of successfully defending any attack. After so much of advances in medical sciences the common cold still exists!
If you know the enemy and know yourself, you need not fear the result of a hundred battles. If you know yourself but not the enemy, for every victory gained you will also suffer a defeat. If you know neither the enemy nor yourself, you will succumb in every battle.
The Art of War - Sun Tzu. Lived: 500-320 BC
[1] 2005 Vulnerability List
[2] WMF Vulnerability – MS Advisory 912840 -
Security Focus - Zero-day WMF flaw underscores patch problems by Robert Lemos – January 12, 2006
[3] Forrester – Large Enterprises Pursue Strategic SOA by Randy Heffner - April 5, 2005
[4] ERP Apps – Technology and Industry Battle heats up by Paul Hamerman, R Wang – June 9, 2005
[5] SAPs Big Bet To Revolutionize App by Erin Kinikin – August 3, 2004
[6] Forrester Wave – Data Encryption Solutions Q3, 2005
Application Security – http://www.appsecinc.com/
Encryption of Data at Rest - http://www.appsecinc.com/presentations/Encryption_of_Data_at_Rest.pdf
DMReview – Information Management: Encryption at Rest
[8] Gartner – http://www.gartner.com/
Future of Enterprise
Cool Vendors in Security and Privacy – March 28, 2005
[9] Forrester – Your Strategic SOA Platform Vision By Randy Heffner – March 29, 2005
Development Roles In The World Of Service-Oriented Architecture – January, 13, 2005
SOAP Vs REST – A Comparison – By Randy Heffner, September 13, 2004
Forrester Wave – Enterprise
[10] Forrester - Trends 2005: Security Convergence Gets Real By Steve Hunt – January 11, 2005
Converged IT And Physical Security: Small But Real – By Laura Koetzle April 15, 2005
[11] CERN – The worlds largest particle physics lab - http://public.web.cern.ch/Public/Welcome.html
[12] Stanford University
[13] Getting closer to the God Particle - http://arafkarsh.blogspot.com/2005_02_01_arafkarsh_archive.html
[14] String Theory - http://www.superstringtheory.com/index.html
[15] What is so peculiar about this year?




No comments:
Post a Comment